A Strategic Framework for Exploiting Competitor Vulnerabilities
May 09, 2025
Your fiercest competitor just suffered its second data breach this year. A legacy player's customer service wait times have doubled. Another competitor's "pricing transparency" initiative was exposed as a smokescreen for fee increases. Meanwhile, that buzzy upstart is desperately downplaying its latest controversy.
Welcome to the era of "We suck less" – a landscape where only 50% of U.S. consumers trust the brands they engage with, and 61% of people globally believe businesses make their lives harder while serving narrow interests.
For visionary revenue leaders, this is not a crisis. Instead, they see the most significant market opportunity of the decade. When strategically exploited, competitor trust failures translate directly to your bottom line: conversion rates lift by up to 50%, customer retention improves by up to 50%, acquisition costs plummet, and price premiums expand by up to 25% against competitors struggling with trust issues.
The strategic imperative is clear: systematically transform your competitors' trust deficits into a competitive advantage.
Strategies For Exploiting Competitive Vulnerabilities
Revenue leaders need a systematic process for identifying and exploiting competitor trust vulnerabilities. This begins with comprehensive competitive trust vulnerability assessments across four critical domains:
Product claims practices: Where competitors overpromise and underdeliver. Counter tactics can include product gap disclosure (being explicit about what your product doesn't do), suitability assessments (helping customers determine if your solution is actually right for them), and realistic expectation setting (providing accurate timelines and results projections).
Accurate product claim translate into reduced refund rates and higher customer satisfaction. Patagonia exemplifies this approach with their "Don't Buy This Jacket" campaign, which explicitly acknowledged the environmental limitations of their products at a time when competitors were making dubious sustainability claims. This transparency created strong conversion advantage with environmentally conscious consumers who became skeptical of competitor greenwashing.
Pricing transparency: Where competitors obscure fees or manipulate pricing structures. When competitors rely on hidden fees, unclear terms, or bait-and-switch pricing tactics, weaponized pricing transparency creates significant trust asymmetry. Counter tactics include total cost calculators (showing actual costs including all fees), guarantee structures (promising no unexpected charges), and simplified pricing models (eliminating the complex fee structures competitors use to disguise costs).
Pricing clarity translates into measurable conversion advantages. Costco's membership model demonstrates this principle. By making all revenue sources transparent (membership fees vs. product margins) and eliminating the complex promotional pricing that frustrates grocery shoppers, the company created trust-based differentiation in a notoriously low-trust industry.
Service quality: Where competitors fail to deliver consistent, empathetic service. As competitors increasingly hide behind chatbots, automated systems, outsource call centers and opaque service policies, service transparency creates powerful trust differentiation. Counter tactics include SLA guarantees (making specific commitments about response times), escalation clarity (having transparent processes for resolving issues), communication consistency (maintaining the same service standards across all channels), locally-based service agents and dedicated relationship managers.
Chewy's customer service approach illustrates this strategy. By offering direct access to human representatives while competitors forced customers through automated systems, publishing their service commitments, and creating transparent escalation paths, they transformed service transparency into a pricing premium in an otherwise commoditized market.
Data privacy practices: Where competitors mishandle, misuse, or fail to protect customer data. With growing concerns about data misuse, privacy transparency creates powerful differentiation against competitors with questionable data practices. Counter tactics includes privacy dashboards (giving customers control and visibility), data minimization policies (collecting only essential information), and third-party audits (providing external verification of privacy claims).
These approaches can be directly linked to revenue impact through conversion rate improvements, particularly with privacy-conscious customer segments. Apple's App Tracking Transparency feature exemplifies this approach, creating clear market differentiation against competitors with more aggressive data harvesting practices.
The Science of Vulnerability Mapping
To identify these vulnerabilities, sophisticated organizations deploy multiple intelligence-gathering tools:
- Sentiment analysis, review mining, and forum monitoring to track customer dissatisfaction
- Industry analyst reports and expert assessments that highlight competitor weaknesses
- Structured interviews with competitors' former employees who can reveal internal practices
- Focus groups and interviews with prospects and lost customers to understand perception gaps
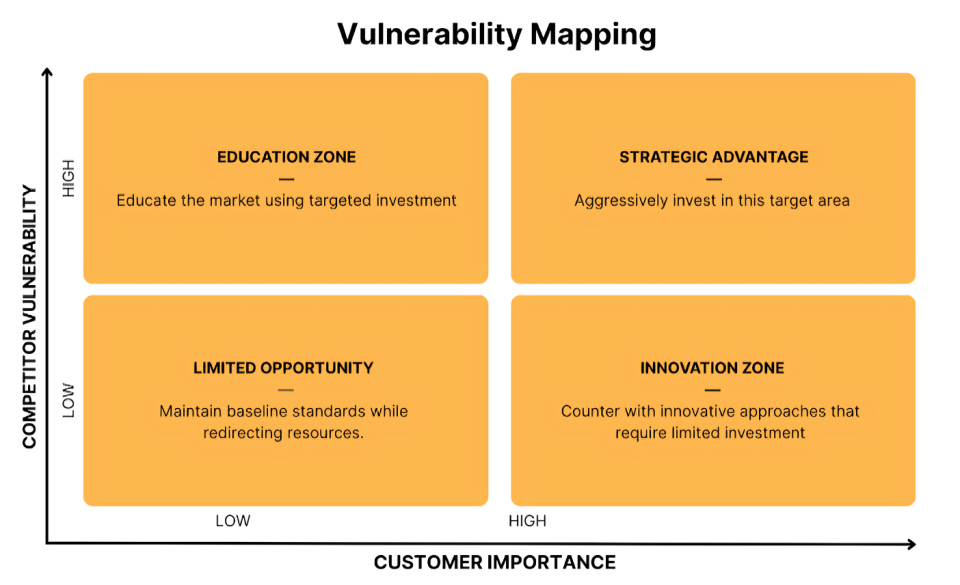
By systematically mapping competitor vulnerabilities against customer priorities, revenue leaders can focus resources on the precise trust gaps that create maximum competitive advantage. The central tool for turning this intelligence into strategic action is the Trust Gap Matrix—a 2x2 framework applied to each trust domain that maps customer importance against competitor vulnerability into four strategic quadrants that determine your trust asymmetry priorities:
Limited Opportunity (Low Customer Importance, Low Competitor Vulnerability): Maintain baseline standards while redirecting resources to more strategic areas. These are the table stakes of trust but won't drive significant differentiation.
Innovation Zone (High Customer Importance, Low Competitor Vulnerability): Trust matters greatly to customers, but competitors maintain relatively strong positions. Counter with innovative approaches that require limited investment to create differentiation in crowded spaces.
Education Zone (Low Customer Importance, High Competitor Vulnerability): Competitors show weakness, but customers don't yet prioritize these areas in decision-making. Educate the market using targeted investment to create future competitive advantage.
Strategic Advantage (High Customer Importance, High Competitor Vulnerability): Customers deeply care about trust, and your competitors have significant weaknesses. Invest aggressively in these high-impact areas to create maximum competitive separation.
Targeting Competitor Trust Gaps with Precision
Why corporate approaches to "building trust" miss the strategic opportunity. Undifferentiated platitudes ("We value your trust"), focus on industry-standard practices, make vague assertions without proof points is like taking a defensive posture rather than creating competitive contrast. When every company claims trustworthiness in similar ways, they become indistinguishable to skeptical consumers, failing to create meaningful differentiation in markets where trust has become a critical competitive battleground. These approaches fail to capitalize on specific competitor vulnerabilities that matter most to customers.
Effective trust asymmetry requires creating clear contrast narratives that highlight specific trust differentiators. Rather than saying "We value your privacy" (generic), a company might say "We never sell your browsing data to third parties, and here's our third-party audit that proves it" (specific trust asymmetry).
Discover Card's "No Annual Fee" campaign exemplifies this approach. Rather than generically claiming to be customer-friendly, they directly attacked competitors' annoying annual fees with a specific, verifiable contrast. Their marketing explicitly highlighted the role of banks–to help consumers save money–to question why their credit cards charged annual fees, which research showed customers deeply resented. The pitch: Discover eliminated them for all of their credit cards.
There are risks to this approach. Highlighting competitor weaknesses can backfire if:
- You attack vulnerabilities that customers don't actually care about
- Your claims aren't credibly differentiated or verifiable
- Your messaging appears opportunistic rather than authentic
- You have similar vulnerabilities that competitors can counter-exploit
Organizations that master this framework develop a distinctive capability to convert widespread market skepticism into targeted competitive advantage. They don't just build trust—they weaponize it through specific contrast narratives that highlight competitor weaknesses in areas that matter most to customers.
For revenue leaders looking to create sustainable advantage in low-trust markets, the message is clear: Generic trust-building is no longer sufficient. The future belongs to organizations that systematically exploit competitor trust vulnerabilities through strategic asymmetry.
In my next post, "Building Competitive Advantage: Systems That Convert Skepticism to Revenue," we'll explore how leading organizations implement this framework through targeted transparency initiatives across four key domains and build systematic capabilities to maintain trust asymmetry over time.

